- Jan 28, 2020
- 851
- 7
- 283
- Language
- English
Vivo Y55 5G, Y75 5G, Y76 5G Dead Boot Repair, and Security Repair successfully
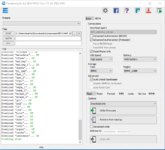
Vivo Y55 5G, Y75 5G, Y76 5G Flashing With Pandora:
Operation logs:
Selected model: Vivo PD2166F (Vivo Y75 5G)
Operation: Flash (Download only)
Software version: 5.0
If BROM was disabled and you want write preloader partition not compatible for this model, phone will bricked. Recovery possible only with ISP mode.
Continue? YES
Parse scatter file... OK
Load Rom Images... OK
Host Power Off... OK
Switch virtual port to NONE... OK
Connect Type-C to HUB... OK
Host Power On... OK
Connect phone to [BOX or PC] in PRELOADER Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek PreLoader USB VCOM_V1632 (Android),usb2ser.sys,3.0.1504.0]
Device found at COM19 [PRELOADER]
Open port... OK
Send start cmd... OK
Get HW code from device... 0989
Get sec config... OK [00000005]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6833]
Currently using Beta/Unsafe operations
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Preloader exist. Skip connection verification.
Get ME ID... OK
ME_ID = 0xCDEF3B10, 0x77C84A0B, 0x1F6FCE70, 0x13B40AF1
Load DownloadAgent... OK
Search DA... OK [11]
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [PRELOADER]
Preloader alive. Skip initializing external RAM
Get device info... OK
UFS CID (FW VER): H9HQ15AECMBDAR (A043)
Advanced Bypass Security... OK
Send preloader... OK
Load DownloadAgent... OK
Search DA... OK [14]
Send 2nd DA... OK
Get device info... OK
UFS INFO:
UFS_CID : H9HQ15AECMBDAR
UFS_FWVER : A043
BLOCK_SIZE: 0x0000001000 (4.00Kb)
UFS_LU0 : 0x0000400000 (4.00Mb)
UFS_LU1 : 0x0000400000 (4.00Mb)
UFS_LU2 : 0x1DCB000000 (119.17Gb)
RAM INFO:
INT_SRAM: 0x0000070000 (448.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
Get scatter info... OK
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... error(STATUS_PARTITION_TBL_NOT_EXIST)
Get scatter info... OK
Verify scatter file... OK
Do NAND BMT remark... OK
Setup download info... OK
Get partition table catagory... OK [GPT]
Read mirror partition table... OK
Generate mirror partition table... OK
Downloading mirror partition table... OK
Read major partition table... OK
Generate major partition table... OK
Downloading major partition table... OK
Download "recovery"... OK
Download "vbmeta"... OK
Download "vbmeta_system"... OK
Download "vbmeta_vendor"... OK
Download "factory"... OK
Download "vbmeta_oem"... OK
Download "vbmeta_vgc"... OK
Download "storage"... OK
Download "metadata"... OK
Download "efuse"... OK
Download "md1img"... OK
Download "md1img_1"... OK
Download "spmfw"... OK
Download "pi_img"... OK
Download "dpm_1"... OK
Download "dpm_2"... OK
Download "scp1"... OK
Download "scp2"... OK
Download "sspm_1"... OK
Download "sspm_2"... OK
Download "mcupm_1"... OK
Download "mcupm_2"... OK
Download "gz1"... OK
Download "gz2"... OK
Download "lk"... OK
Download "lk2"... OK
Download "boot"... OK
Download "logo"... OK
Download "dtbo"... OK
Download "tee1"... OK
Download "tee2"... OK
Download "super"... OK
Download "cache"... OK
Download "userdata"... OK
Flashing done!Vivo Y55 5G, Y75 5G, Y76 5G IMEI Repair With Pandora:
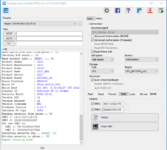
Operation logs:
Selected model: Vivo PD2166F (Vivo Y75 5G)
Operation: Repair
Software version: 5.0
Host Power Off... OK
Switch virtual port to NONE... OK
Connect Type-C to HUB... OK
Host Power On... OK
Connect phone to [BOX or PC] in PRELOADER Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek PreLoader USB VCOM_V1632 (Android),usb2ser.sys,3.0.1504.0]
Device found at COM19 [PRELOADER]
Open port... OK
Send start cmd... OK
Get HW code from device... 0989
Get sec config... OK [00000005]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6833]
Currently using Beta/Unsafe operations
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Preloader exist. Skip connection verification.
Get ME ID... OK
ME_ID = 0xCDEF3B10, 0x77C84A0B, 0x1F6FCE70, 0x13B40AF1
Load DownloadAgent... OK
Search DA... OK [11]
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [PRELOADER]
Preloader alive. Skip initializing external RAM
Get device info... OK
UFS CID (FW VER): H9HQ15AECMBDAR (A043)
Advanced Bypass Security... OK
Send preloader... OK
Load DownloadAgent... OK
Search DA... OK [14]
Send 2nd DA... OK
Get device info... OK
UFS INFO:
UFS_CID : H9HQ15AECMBDAR
UFS_FWVER : A043
BLOCK_SIZE: 0x0000001000 (4.00Kb)
UFS_LU0 : 0x0000400000 (4.00Mb)
UFS_LU1 : 0x0000400000 (4.00Mb)
UFS_LU2 : 0x1DCB000000 (119.17Gb)
RAM INFO:
INT_SRAM: 0x0000070000 (448.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : vivo
Product Manufacturer : vivo
Product Model : V2127
Product Name : 2127_EEA
Product Device : 2127
Product Board : k6833v1_64
Board Platform : MTK6833
Build ID : SP1A.210812.003
Build Date : Fri Dec 2 20:33:27 CST 2022
Display ID : Funtouch OS 12 Global
Security Patch : 2022-12-01
Version SDK : 31
Version Release : 12
Version Codename : REL
Firmware Version : 3.19.7
Userdata FS Type : F2FS
Reading security from phone... OK
IMEI 1: 111111111111119
IMEI 2: 222222222222228
Set new IMEI to:
IMEI 1: 350711558237556
IMEI 2: 356086278237556
Searching security key... found! [3]
Writing security to phone... OK
Repair Security done!
